Analysis of Cryptocurrency Impact on Ransomware Payment Using Machine Learning.
Muhammed Nurudeen Usman || Adebayo Abdulganiyu KEJI

Abstract
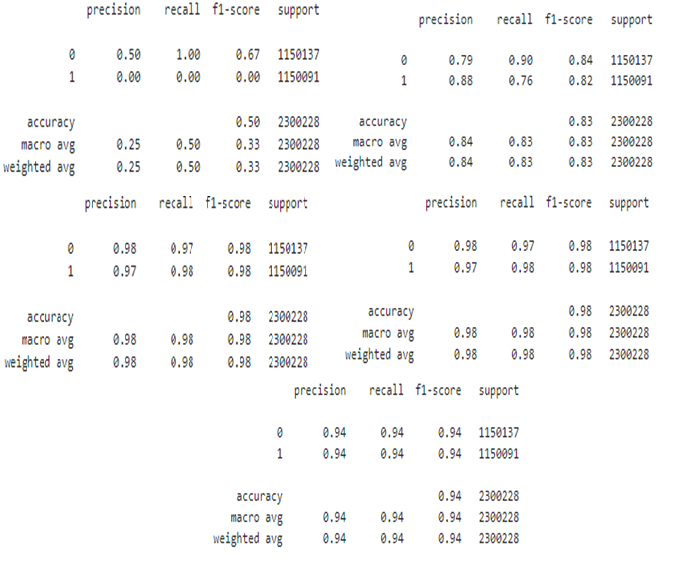
The Internet has grown indispensable to daily life as computers and the Internet become more commonplace. The International Telecommunication Union (ITU) estimates that over 67% of people on the planet will have access to the internet by 2023. It is false to say that the Internet is innately good or bad. Cybercriminals have utilized malware as a tool to further their objectives. Malware has been used to initiate a range of security attacks. Cybercrimes, such as malware attacks, Ponzi schemes, phishing scams, and other illegal activities, have increased in number as cryptocurrency popularity has increased. Since cryptocurrency payments are anonymous, it is challenging to recognize and categorize ransomware transactions on the network. In this paper, I presented the use of machine learning to detect ransomware payments by using both conventional and deep neural network models. With accuracy, f1 score, precision, and recall topping at 98% for decision tree and random forest, it is evident that the two models performed better than the others. This research has effectively improved the functionality of the current models for ransomware transaction detection.
Methodology
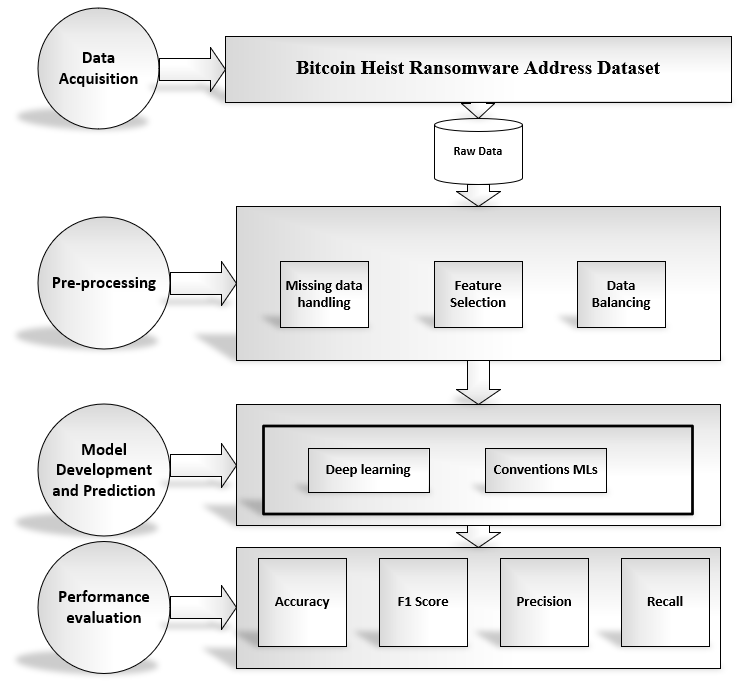
This study's part highlights the various methods, procedures, and approaches that were employed to meet the predetermined objectives and aims, along with the design framework that served as the research's compass. This section explains the process for distinguishing between normal and ransom payment transactions using machine learning, with capability of high level of recall, precision, F1 score and accuracy. The main concept of this research methodology is the application of ML to identify cryptocurrency payments (Bitcoin) on ransomware.
Conclusion
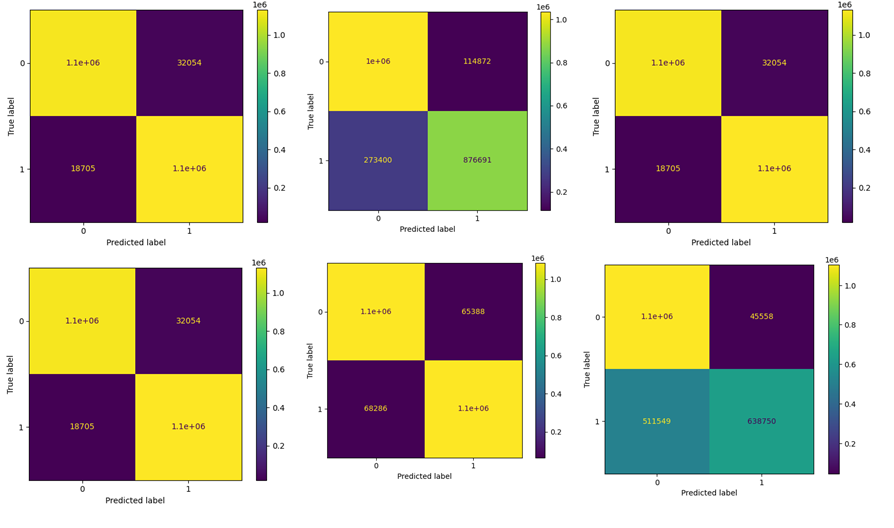
In this study we presented the detection of ransomware payment using machine learning technique by developing conventional and deep neural network models. The dataset used in this work was provided by the UC Irvine Machine Learning Repository. For the dataset, a single transaction every day, or every 24 hours, was gathered over a nine-year period between 2018 and 2009. This dataset contains 2916697 instances total, each with 10 characteristics. For implementation concerns, this dataset was preprocessed into a binary classification issue. To determine which features were salient—that is, which features showed a strong correlation with the target variable—the ExtraTreeClassifier algorithm was utilized. We then balanced the data class using a suitable data-balancing technique called SMOTE. Furthermore, the machine learning models—KNN model, XGboost, Decision tree, Random forest, and LSTM—were subsequently implemented. These models were trained using the training dataset, and then they were assessed using the testing dataset. It is clear that the Decision tree and Random forest models fared better than the others, with accuracy, f1 score, precision, and recall peaking at 98% for both models. When XGBoost was compared to decision trees and random forests, it obtained near ideal performance with 94% of all its performance criteria. The MLP model performs the worst, with an accuracy rate of only 50% and an inability to detect any ransomware transactions. Furthermore, the deep neural network (LSTM) has an F1-Score of 75%, recall of 76%, accuracy of 81%, and precision of 76%. This study has successfully enhanced the performance of the existing models in the detection of ransomware transaction, thus, achieved the aim and objective of the study.